HTC has revealed a follow up to the successful HTC One Android-based smartphone that went on sale earlier in the year called the HTC One Mini, which largely stays true to to the spec and feature list of its larger sibling.
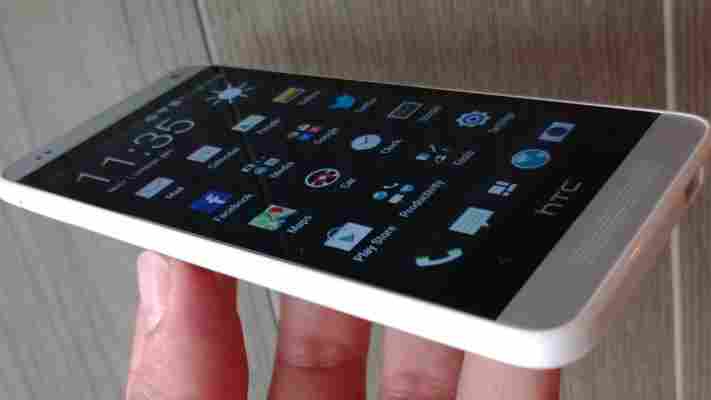
Available in silver or black, it keeps the same ‘zero-gap’ construction and aluminium design of the original, which also means that it retains the HTC Boom Sound speakers on the front of the device.
Obviously, the largest difference is the smaller screen size – reduced from 4.7-inches to 4.3-inches – which has a 720p ( which we already knew from leaks ) resolution rather than the 1080p of the HTC One.
Other key hardware specs include a dual-core (rather than quad-core like on the HTC One) 1.4GHz processor, the most recent Jelly Bean (4.2.2) version of Android. A spokesman for the company told The Next Web the NFC capabilities of the HTC One had to be dropped for the Mini as they couldn’t fit the chip inside the chassis. It will also play nicely with all the same 3G/4G bands as the HTC One.
While it keeps the same Ultrapixel sensor as its sibling, it actually brings a few updated camera software features, such as being able to select from more themes when creating ‘Highlights’ (automatically created 30 second ‘movies’ of your pictures) and the ability to set them to your own music. HTC said the software would analyze the first 30 seconds of the chosen song and try and match the picture changes of the Highlight reel to the same beat.
HTC said these software options would also be available on HTC One handsets that have been updated to Android 4.2.2.
The handset will initially be offered in the UK and Germany “from August” within Europe, before being gradually rolled out more widely. Pricing is apparently up to the operators to set, according to an HTC spokesman, but he did say it would come in “about two price-points below” the HTC One in terms of operators’ ranges.
Its no secret that since a couple of hit handsets a few years back, HTC has struggled to remain relevant in the smartphone market, but the HTC One seems to have provided a well-timed hit for the company. A spokesman tells us that it is the widest ranged product HTC has ever released and so far has been made available in 181 countries across 583 different operators.
Netflix brings the “Just for Kids” user interface to the iPad, Android tablet support forthcoming
Video streaming giant Netflix today announced that it is bringing its “Just for Kids” viewing experience to the two latest versions of the iPad, with support for the original iPad and Android tablets coming ‘later this year’.

Netflix “Just for Kids” is a kid-friendly (duh) section with movies and TV shows that have been deemed appropriate for kids aged 12 and under, sporting a user interface that comes with supersize images of their favorite characters and genres.
The company claims its unique technology makes for a personalized experience for each member, based on taste and favorites.
“Just for Kids” was originally launched in August 2011, and Netflix said at the time that it would bring the experience to the iPad. Took them a while, but this is the first time “Just for Kids” was customized for a mobile device.
The company recently brought the “Just for Kids” section to the Xbox 360 – it had already been available on the Netflix website and on other gaming and entertainment systems like Nintendo Wii , Apple TV and PS3.
It’s also available on some Smart TVs, Blu-ray players and streaming media players.
Launching the experience on the iPad is easy as pie: simply click the new “Just for Kids” button in the upper left hand side of the Netflix App.
Image credit: Ryan Anson for AFP / Getty Images
Not just Samsung: Other Android phones can be remotely wiped by hackers, here’s how to check yours
Yesterday we reported about a flaw in Samsung’s Touchwiz UI that allowed for data wiping, among other nasties . The good news is that the flaw has already been patched . The bad news is that self-described general geek Dylan Reeve says it’s not just limited to Samsung devices.

Reeve explains how the remote Unstructured Supplementary Service Data ( USSD ) vulnerability affects many phones, and he has personally verified it on an HTC One X (running HTC Sense 4.0 on Android 4.0.3) and a Motorola Defy (running Cyanogen Mod 7 on Android 2.3.5). Reports suggest the Sony Xperia Active and the Sony Xperia Arc S are also affected, our very own Nick Summers confirms his HTC Desire running Android 2.2 is vulnerable, and the list likely doesn’t stop there. As such, Reeve quickly put together a Web page you can use to check if your Android device is vulnerable to being remotely wiped by hackers: dylanreeveom/phone.php .
So, how is the vulnerability exploited? Reeve explains the root of the problem is the standard Android dialer, the vulnerability for which was identified and patched three months ago :
Phones support special dialing codes called USSDs that can display certain information or perform specific functions. Among these are common ones (*#06# to display IMEI number) and phone specific ones (including, on some phones, a factory reset code).
There is a URL scheme prefix called tel: which can be used to hyperlink phone numbers. Clicking on a tel: URL will initiate the phone’s dialer to call that number.
In some phones the dialer will automatically process the incoming number, thus requiring no user interaction. If it’s a USSD code then it will be handled exactly as if it had be keyed in manually, meaning it will be executed automatically.
A tel: URL can be used by a hostile website as the source for an iframe (and potentially other resources like stylesheets or scripts). It may then be loaded and acted upon with no user intervention at all.
The potential impact of this issue is thus limited to whatever USSD codes can be executed on a given phone (for example, if the Factory Reset one isn’t present, then that’s out of the question), as well as how tel: works on a given phone.
Although this security hole has been plugged, not every manufacturer has patched it, not every carrier has pushed out a fix, and of course not every consumer has installed all available updates. It is possible that any Android phone using the standard dialer from three months ago, or a dialer based on it, can be hacked.
So, what can you do about it? Aside from installing the latest patches for your Android device, Reeve has a suggestion: install another dialer. You can either set one that doesn’t exhibit the risky behaviour by default, or just have a second one installed so that a “Complete action using” prompt shows up whenever a website tries to hack your device, at which point you can just cancel or use the alternative dialer.
This workaround is only possible because Android allows you to install third-party dialers. The one above can be found on the official Google Play store . Since it does not take action on the incoming USSD code, Dialer One lets you avoid having your device hacked. If you prefer a different dialer, test it with Reeve’s site to make sure it doesn’t handle tel: URLs without direct user interaction.
Image credit: stock.xchng
